Author: Marçal Santos, vCISO | +20 Years Cybersecurity Experience
If you’re a CEO or CTO of a B2B SaaS in the 05–200 employee range, this is for you. I’ll show you the shortest path to a legitimate ISO 27001 certificate that actually helps you close deals and reduce risk—without burning your team out.
Why ISO 27001 Feels Hard (And Doesn’t Need To)
What derails most teams:
- Jargon: Clauses, Annex A, “SoA,” four control themes, risk appetite—it’s a lot.
- Tool trap: Buying a platform (Vanta/Drata, etc.) and assuming it replaces thinking. It doesn’t. It helps, but it doesn’t decide scope, risk, or controls.
- Audit anxiety: Auditors aren’t trying to trick you, but they do expect a real management system, not policy theater.
I’ve been in the trenches 20 years. You don’t need to boil the ocean or stop shipping. You need a lean, risk-first approach with clear ownership and repeatable evidence. Think “minimum viable ISMS” that’s strong enough to pass Stage 2 and simple enough to run every quarter.
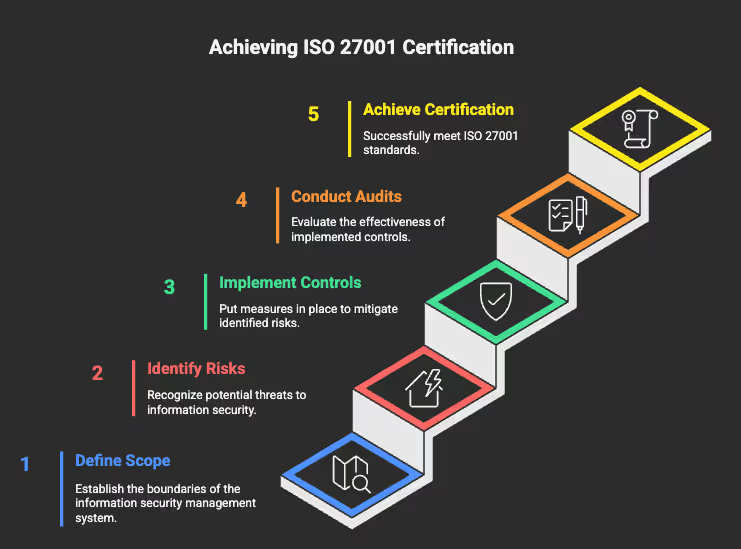
The Simple Framework: Five Steps to Certification
I use this with SaaS clients to go from zero to certified:
- Scope: Define what’s in and out—precisely.
- Risks: Identify what can go wrong, and how you’ll treat it.
- Controls: Pick the right Annex A controls and implement them pragmatically.
- Evidence: Prove it with living records, not screenshots stuffed in folders.
- Audit: Do internal audit and management review, then pass Stage 1 and Stage 2.
That’s it. Everything else fits inside those five.
The How-To (Tactical, Founder-Friendly)
A) Scope: Draw the smallest circle that still satisfies customers
If you try to cover your entire company on day one, you’ll slow to a crawl. If you scope too narrowly (and exclude critical systems), auditors and customers will push back.
What to include:
- Your production product(s), the cloud environment(s) they run in (AWS/GCP/Azure), and the teams and tools that support them.
- Supporting processes like incident response, change management, vendor management, and business continuity.
What can often be out of scope (initially):
- Experiments, defunct systems, legacy internal tools not touching customer data.
- Non-production systems that are truly isolated from prod data.
Artifacts auditors expect:
- Scope statement with boundaries, locations, assets, and justifications for exclusions.
B) Context and Leadership: Make it a business initiative, not an IT project
ISO 27001 is a management standard. Auditors want to see leadership commitment and business alignment.
Define objectives with measurable targets:
- Example: “Reduce critical vulnerabilities in prod to zero within 30 days of discovery; maintain 100% MFA coverage; complete vendor reviews within 10 business days.”
- Identify interested parties and requirements:
- Customers (enterprise contracts), regulators (e.g., GDPR), partners, employees.
Assign roles:
- ISMS owner (often your vCISO or Head of Security), control owners (Eng, IT, People Ops, Legal), executive sponsor (CEO/CTO).
Artifacts:
- Information Security Policy signed by leadership.
- ISMS Objectives and metrics.
- Roles and responsibilities (RACI is fine).
C) Risk: The engine that drives everything
ISO 27001 is risk-based. The controls you choose must trace back to risk.
Build a practical asset inventory:
- Systems (prod clusters, CI/CD), data stores (RDS, S3), code repos, endpoints, vendors (Auth0, Stripe, Segment), accounts (AWS org).
Identify threats and rate risk:
- Use a simple likelihood/impact scale (e.g., 1–4). Avoid overcomplication.
- Example risks: secret leakage in CI logs, misconfigured S3 bucket, privilege creep in IAM, dependency vulnerabilities, vendor breach.
Decide treatment:
- Mitigate (control), accept (document rationale), avoid (change design), transfer (contract/insurance).
Artifacts:
- Risk methodology (one page).
- Risk register with owners and treatment plans.
- Review cadence (quarterly is common).
D) Controls: Pick the right ones from Annex A (93 controls, 4 themes)
Annex A (aligned with ISO 27002:2022) groups controls into Organizational, People, Physical, and Technological. You don’t need all 93; you need what your risks require. Document inclusions/exclusions in the Statement of Applicability (SoA).
For a cloud-native B2B SaaS, these are the usual high-impact controls:
Identity and access management:
- SSO + enforced MFA across critical systems (IdP integrated everywhere).
- Least privilege: role-based access, quarterly access reviews.
- Automated offboarding tied to HRIS.
Secure SDLC and change management:
- Branch protections, mandatory code review, signed commits optional bonus.
- CI/CD with SAST/DAST and dependency scanning; block on critical vulns.
- Infrastructure-as-code scanned pre-deploy; change tickets linked to PRs.
Vulnerability and patch management:
- Weekly scans on apps and images; 30/60/90-day SLA by severity.
- Endpoint patching via MDM/EDR with encryption and screen lock enforced.
Logging, monitoring, and detection:
- Centralized logs (CloudWatch, Datadog) with retention.
- Alerts for auth anomalies, privilege escalations, config drift.
Encryption and key management:
- TLS 1.2+ in transit; KMS-managed encryption at rest; key rotation policy.
Backup and continuity:
- Automated backups; tested restore; defined RTO/RPO.
- Business Continuity and Disaster Recovery plans with at least one tabletop test.
Supplier risk:
- Maintain vendor inventory; security reviews for critical vendors.
Incident response:
- Playbooks for auth compromise, data exposure, ransomware.
- On-call rota, severity definitions, comms plan; run a tabletop and keep minutes.
HR and awareness:
- Background checks (where legal), NDAs, onboarding/offboarding checklists.
- Annual training plus phishing simulations.
Physical (lightweight if fully cloud-based):
- Office access controls; device secure storage; visitor process.
Artifacts:
- Statement of Applicability (SoA) mapping to risks and justifying exclusions.
- Control procedures/playbooks and logs that show they run.
E) Evidence: Make it living and lightweight
Auditors look for two things: that you’ve defined what you do, and that you actually do it on a schedule.
Evidence that plays well:
- Access review records with findings and remediation.
- Screens or exports showing MFA and SSO coverage.
- Vulnerability scan reports and remediation tickets tied to SLAs.
- Incident tabletop minutes with action items and owners.
- Backup restore test logs with timestamps.
- Vendor reviews with risk ratings and contracts.
- Use tools to automate, not to abdicate:
Platforms like Vanta/Drata are great for collecting evidence, reminding owners, and mapping to controls. They won’t choose your scope, write your risk register, or run your tabletop. Use them as the evidence layer atop a thoughtful ISMS.
F) Internal Audit and Management Review: Your dress rehearsal
Before any external auditor shows up, you must audit yourself and review results with leadership.
- Internal audit:
- Check each clause (4–10) and sampled controls. Find nonconformities before the auditor does.
- Produce a report with corrective actions and due dates.
- Management review:
- Present metrics, incidents, audit results, risk changes, vendor issues.
- Record decisions: resource changes, policy updates, objective resets.
G) The Certification Audit: What actually happens
Pick the right auditor:
- Choose an accredited Certification Body (CB) with experience in SaaS.
Note: Secureleap can help you with Auditors
Stage 1 (documentation/readiness):
- Auditor checks scope, policies, risk methodology, SoA, internal audit, management review. They’ll flag gaps to fix.
Stage 2 (implementation/effectiveness):
- Evidence sampling and interviews with control owners. Expect “show me” moments: access reviews, tickets, logs, training records, incident drills.
After certification:
- Year 2 and 3 surveillance audits (lighter). Year 4 recertification.
H) A realistic timeline for a 5–200 person SaaS
- Weeks 1–2: Scope, context, objectives, roles, risk methodology.
- Weeks 3–6: Risk register, control selection, SoA, policy drafting.
- Weeks 4–10: Control implementation and evidence runs (access review, vuln scan cadence, IR tabletop, backup restore test).
- Weeks 9–10: Internal audit and management review.
- Weeks 11–13: Stage 1 audit; remediate.
- Weeks 14–16: Stage 2 audit; address findings, receive certificate.
If you already have decent security hygiene (SSO/MFA, CI/CD discipline, vendor tracking), you can compress this. If you’re starting from scratch, give yourself a quarter and a half.
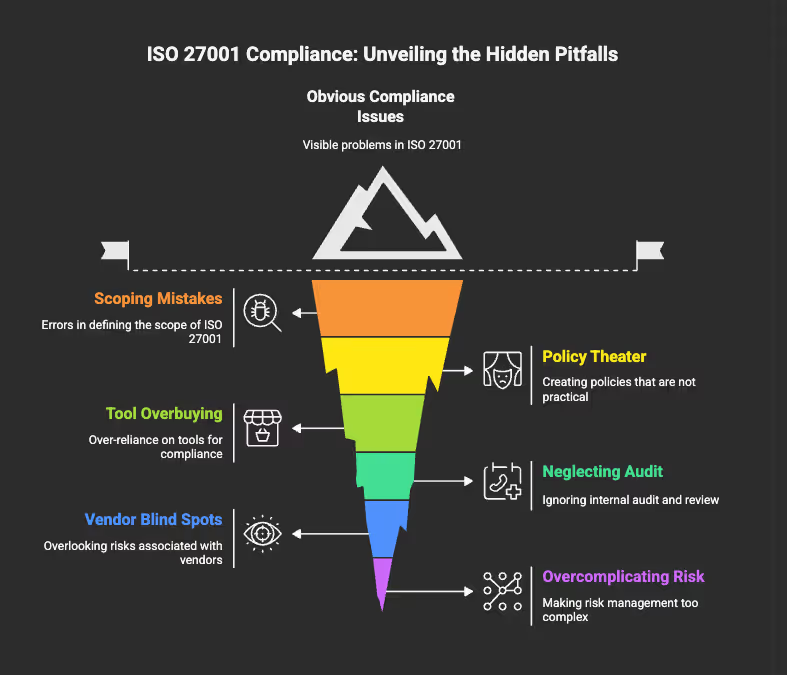
5) Common Pitfalls (And How To Avoid Them)
1) Scoping mistakes
- Too wide: Including every team, every office, every legacy tool. You drown in complexity and stall.
- Too narrow: Excluding the primary product environment or critical vendors. Customers and auditors will challenge it.
- Fix: Scope to the product(s) and systems that process customer data. Add the rest next year.
2) Policy theater
- Writing perfect policies that don’t match reality. Auditors quickly sniff this out.
- Fix: Start with what you already do, tighten where needed, and schedule activities you’ll actually perform (quarterly access reviews, monthly vulnerability scans, annual BCP test).
3) Tool overbuying
- Assuming a platform equals compliance. It doesn’t decide risk or fix process gaps.
- Fix: Use tools to automate evidence and reminders, but do the thinking: risk register, SoA justifications, real drills.
4) Neglecting internal audit and management review
- Skipping these is a guaranteed nonconformity.
- Fix: Treat them like board meetings. Put them on the calendar, prepare metrics, and record decisions.
5) Vendor blind spots
- Critical third parties (Auth, Cloud, Payments) with no formal review. If they fail, your controls fail by proxy.
- Fix: Maintain a vendor inventory with criticality ratings, review SOC 2/ISO reports, track DPAs, and document risk exceptions.
6) Overcomplicating risk
- 50-page risk methodologies, qualitative-quantitative hybrids, and Monte Carlo models that nobody updates.
- Fix: Simple 1–5 scales, plain language threats, clear owners, quarterly updates. Speed beats elegance.
6) Strategic Takeaway: ISO 27001 Is a Revenue Enabler, Not a Checkbox
When done right, ISO 27001 becomes a sales asset and an operating rhythm. It shortens security questionnaires, unlocks enterprise deals, and gives you confidence that the boring-but-critical stuff happens on time. You’re not just earning a logo—you’re building a trustworthy system that scales with your product and your pipeline.
7) What “Good” Looks Like (A Quick Self-Check)
- Scope is tight and defensible. Everyone knows what’s in and out.
- Risks are documented, owners assigned, and treatments aligned with reality.
- SoA clearly maps controls to risks with honest exclusions.
- Evidence exists because the process exists—no screenshot scavenger hunts.
- Internal audit and management review are on the calendar with minutes and actions.
- You can explain your ISMS in 3 minutes to a customer—and it sounds like how you actually run the business.
8) If I Were You, I’d Do This Next Week
- Day 1: Write a one-page scope and get leadership sign-off.
- Day 2–3: Build a first-pass asset and vendor inventory. Identify your top 10 risks.
- Day 4: Draft your SoA with initial inclusions/exclusions. Tie to those risks.
- Day 5: Schedule your first access review, vuln scan, IR tabletop, and backup restore test. Put recurring cadences in the calendar.
- Week 2: Kick off internal audit prep and choose an accredited auditor. Lock Stage 1 dates.
- Weeks 3–4: Run the activities, collect evidence in your compliance platform or shared workspace, and close obvious gaps.
Tools help, but sequencing and ownership win. That’s the difference between spinning for 6–9 months and certifying in a quarter.
Ready to accelerate your ISO27001 compliance journey without the usual headaches and budget overruns?
At SecureLeap, we've revolutionized the compliance process by bundling everything you need into one seamless experience:
✅ Platform Licenses: Direct access to Vanta, Drata, or Secureframe at competitive rates
✅ Expert vCISO Guidance: 20+ years of hands-on compliance experience
✅ Audit Services: Vetted auditor network with proven track records
✅ Ongoing Support: Continuous monitoring and maintenance to ensure sustained compliance
Why choose SecureLeap over managing multiple vendors?
• Single Point of Contact: No more juggling between platform support, consultants, and auditors
• Transparent Pricing: Fixed-fee packages with no surprise costs or scope creep
• Ongoing Partnership: We're with you for renewals, expansions, and additional certifications
Don't let compliance slow down your enterprise sales momentum. Get a personalized compliance roadmap and pricing in just 30 minutes.
Book Your Strategic Compliance Consultation →
Or
Contact us using this form.






